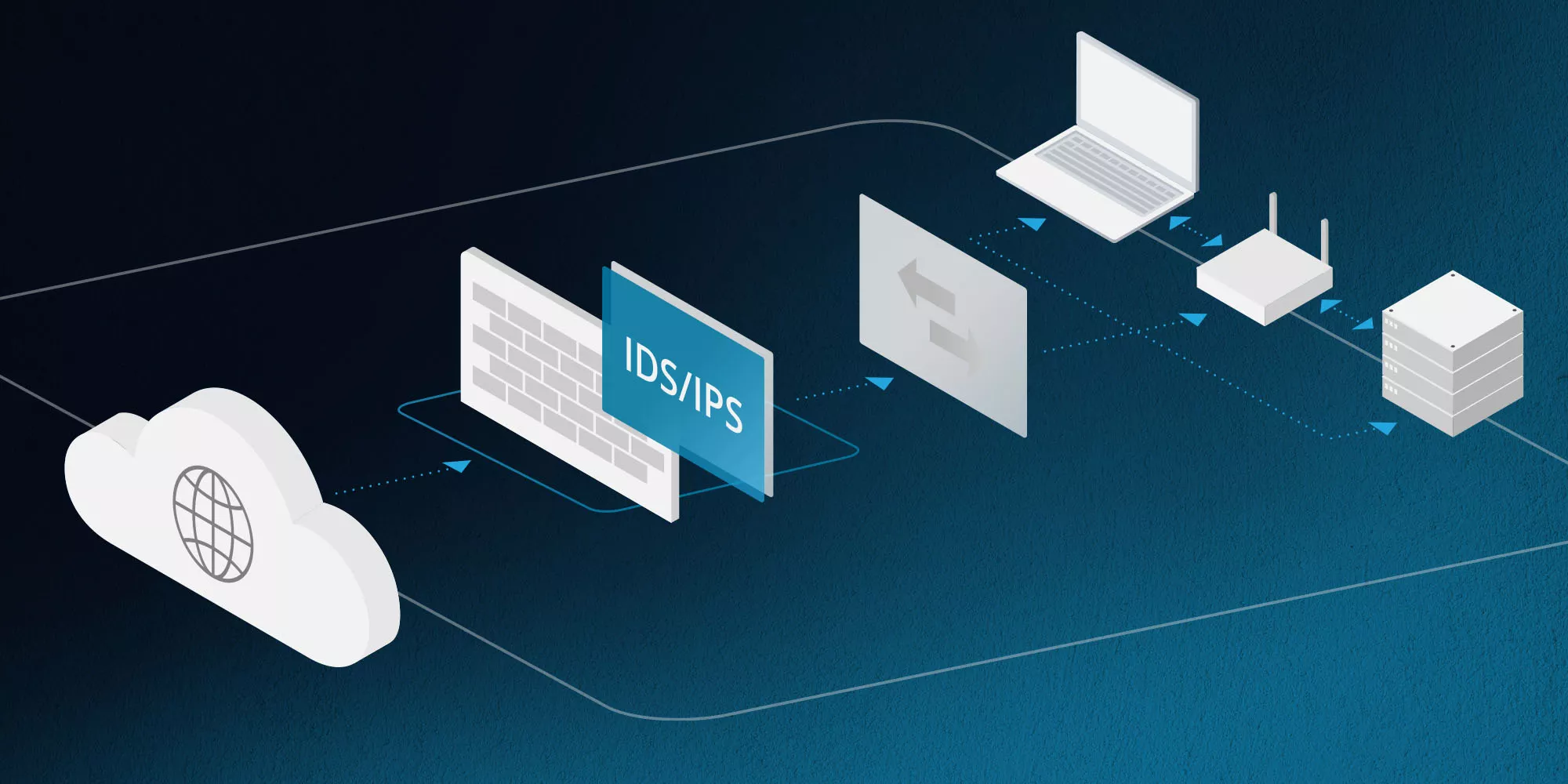
IDS and IPS are critical cybersecurity tools that allow organizations to detect attacks, alert them of them, and take action in real-time. This helps prevent damage, speeds up incident remediation, and enables businesses to stay compliant.
Both solutions monitor network traffic, alert you when they find a potential threat, learn and analyze patterns, and log events. But what distinguishes them is how they respond to threats.
What is an IDS?
In general, an IDS monitors the network for anomalies. It does this by analyzing the data passing through the web and comparing it to a list of rules and patterns. An alert is sent to a system administrator if it finds a match. The administrator can then take steps to address the threat and prevent any further damage.
According to cybersecurity training institute SANS experts, IDS technologies are necessary for any security strategy. However, implementing them can be complex and costly. This is why many organizations don’t use IDS as a standalone solution but instead opt for a complete suite of security capabilities or a single security platform with intrusion detection built-in.
There are two main types of IDS: host-based and network-based. The difference between the two refers to where sensors for the IDS are located: on a host/endpoint or a network.
Host-based IDS sensors analyze activity on individual hosts or endpoints. This can include everything from detecting attempts at system logins to checking for the integrity of files on a host. It also monitors the traffic on a network to detect signs of unauthorized activity. Lastly, it can see problematic traffic for specific software (for example, if an IDS sensor detects a signature-based attack against a company’s Firefox browser). It’s important to note that IDS does not stop attacks once they occur or prevent them from happening in the future.
What is an IPS?
The IPS differs from the IDS in that it takes action to protect the network when a threat is detected. Often, an IPS will block malicious traffic from entering the network, close loopholes in the system and reconfigure existing firewall rules to prevent future attacks. This can be done via an alarm, dropping detection packets, resetting a connection or terminating sessions. Most IPS solutions also record information about observed events and produce reports.
Typically, IPS solutions analyze real-time network traffic to compare it against known attack patterns and signatures. This helps a company detect brute force attacks, DoS (denial of service) attacks and vulnerability exploits. When a new vulnerability is discovered, there is often a window of opportunity for attackers to exploit it before a security patch can be applied. An IPS can quickly stop these types of attacks in its tracks.
Many IPS solutions are designed to be in-line, but some are also incorporated into next-generation firewalls. A few standalone IPS solutions exist, including appliance-based and cloud-native systems. Choosing the best solution for your business depends on your needs and the size of your security department. A standalone IPS will require significant computing resources to perform traffic inspections. This is a big consideration when selecting an IPS for your business, as most systems have compute limitations that may impact performance.
How do IDS and IPS work?
IDS vs IPS solutions monitor network traffic to detect suspicious activity. They use signature-based or behavior-based detection to look for patterns of deviation from normal traffic that could indicate an attack. Alerts the IDS or IPS generates are sent to security teams for further investigation. Many large organizations also deploy security tools like Security Information and Event Management (SIEM) systems to provide context for these alerts.
A common problem with IDS solutions is false positives – when the IDS identifies legitimate activity as malicious. This is because attackers try to hide their activities by using techniques like address spoofing, fragmentation, and pattern evasion. However, this doesn’t mean IDS is ineffective – it offers valuable protection against attacks.
The biggest limitation of IDS and IPS is that they only take action on the traffic they can inspect. This is a significant issue with modern networks that often use encryption to protect data. Some IDS or IPS tools may be able to decrypt this traffic to perform further inspection, but this can significantly impact performance and can introduce new vulnerabilities in the process.
Thankfully, next-generation IDS and IPS tools offer better visibility into network traffic. This allows them to identify malicious activity that would not be detected by older IDS or IPS solutions. This enables them to take additional action on the flow, such as blocking it or terminating sessions. This is one reason why next-generation firewalls typically include IDS or IPS capabilities.
Which is better for my network?
The best IDS or IPS solution for your network will be the one that fits your specific needs and integrates with your broader security strategy. The right tools will provide the visibility and capabilities your team requires to detect and respond to the most advanced threats.
IDS and IPS can be built into a router, firewall or gateway device to offer protection without impacting network traffic flow. This approach is also useful in reducing the risk of false positives, which could have an adverse impact on your organization.
An IDS that monitors traffic will look for patterns and activity that match the signatures of known attacks. This method is effective for detecting established, less sophisticated threats but may fail to recognize zero-day attacks that don’t have pre-existing attack signatures.
An IPS will actively stop or remediate malicious traffic. This can include triggering an alarm, dropping detected packets, resetting the connection or blocking traffic from that offending source. Some IPS solutions can be configured to alert the IT staff of any suspicious activity. They may even decrypt encrypted traffic, perform a manual or automated analysis of suspected malware or send the malicious code to a sandboxing tool for further investigation. This feature is especially useful in preventing attacks that bypass firewalls and other traditional security measures. It is often referred to as a second line of defense.